Software Security Best Practices
Software Security Best Practices: Threat Modeling
By SAFECode Executive Director Steve Lipner
TechTarget – Search Security
Every year, hundreds of thousands of software developers join the workforce without a basic knowledge of security. The burden of educating and training developers on software security is left to the development organizations that hire them.
While development organizations can and should train their employees on company-specific tools and processes, a basic understanding of the nature and importance of software security, and the sources of vulnerabilities, is as fundamental as other aspects of computing such as data structures or performance. Today, I’ll examine one key aspect of software security – threat modeling – that is a fundamental practice that’s part of a secure development program.
At one level, everyone threat-models all the time, such as when you choose what clothes to wear based on the weather, or take steps to protect your parked car against vandalism. Simply put, a threat model first illustrates all the components and sub-components that make your system work, then considers the risks along with the possible mitigations and allows you to decide on an acceptable course of action.
Within a secure software development process, threat modeling is part of software design. Preparing the model requires a good understanding of the system, and logically the model needs to change to reflect any changes in the understanding, or the system. Because the model needs to evolve, a repeatable approach to threat modeling is required to ensure consistency. In the example of car vandalism, the threat model would take into consideration potential adversarial events such as vandals deliberately scratching car bodywork, stealing wing mirrors and smashing windows.
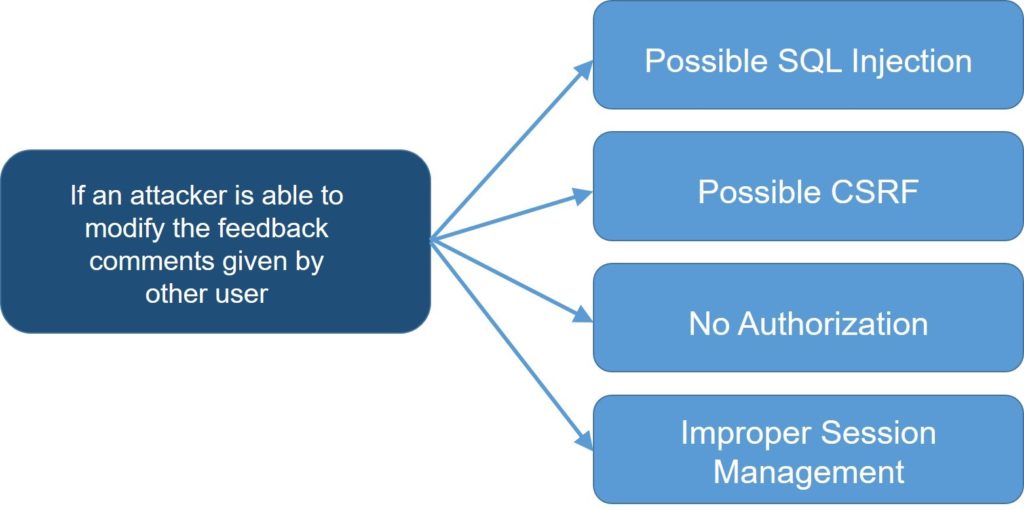
A threat model works by describing a software system and then enumerating and evaluating potential events to assess their impacts. If necessary, the system design can be modified to prevent them or mitigate their consequences. One threat modeling approach is to create an attack tree model that identifies the issues with the most risk first.
The diagram above is a representation of a sample attack tree, which illustrates the potential vulnerabilities that could result from a specific weakness within the application that is being threat-modeled. Once threat modelers identify the potential vulnerabilities, they can devise mitigations that will help to minimize the risks associated with those weaknesses or eliminate them altogether.
Risks that have both security and business impacts will receive the highest priority in a threat model. For example, a security breach that impacts the company’s brand may also result in business losses.
Free resources are available to help organizations and developers understand the fundamentals of threat modeling. For example, SAFECode’s tactical threat modeling white paper discusses how to examine a design, review its data flow diagram, create an attack tree, and understand the attack tree’s implications.
By giving software developers, and not just security specialists, a leg up on the fundamentals of threat modeling, organizations can help ensure their development teams strengthen their software security assurance practices. Over time, the development team will gain the skills to create and analyze many threat models on its own, helping to scale the secure development process and improve its efficiency.
Steve Lipner is the executive director of SAFECode (The Software Assurance Forum for Excellence in Code). Lipner brings more than four decades of experience in software security assurance. He led Microsoft’s Security Development Lifecycle team and was responsible for corporate supply chain security strategies and policies regarding government evaluation of Microsoft security products. A member of the National Academy of Engineering, a Fellow of The International Information System Security Certification Consortium (ISC)², and a National Cyber Security Hall of Fame inductee, his contributions to software assurance have influenced the entire security sector. He is named as an inventor on 12 U.S. patents in the field of computer and network security. In addition, he co-authored the book, The Security Development Lifecycle.